About Me

- tsoorad
- This is a blog for John Weber. One of my joys in life is helping others get ahead in life. Content here will be focused on that from this date forward. John was a Skype for Business MVP (2015-2018) - before that, a Lync Server MVP (2010-2014). I used to write a variety of articles (https://tsoorad.blogspot.com) on technical issues with a smattering of other interests. I have a variety of certifications dating back to Novell CNE and working up through the Microsoft MCP stack to MCITP multiple times. FWIW, I am on my third career - ex-USMC, retired US Army. I have a fancy MBA. The opinions expressed on this blog are mine and mine alone.
2010/12/18
2010/12/16
Pre-sales project information
When you are in front of clients in the pre-sales mode, you need good, solid information that you can relate. And the information needs to come from reliable, quotable resources. This article on Forbes.com presents an initial analysis of a new McKinsey report on collaboration. I encourage you to track down the actual report so you dig out the nuggets that will help you be more successful. There is nothing in this particular article that is vendor specific; rather, the information is business related and gives quantifiable data points using common metrics. Perfect for creating credibility and focusing the discussion on business requirements and pain points.
2010/12/06
Lync Project Elements
Part of being a consultant in knowing what needs doing and what does not need doing – and this is per project. However, there is always the starting, generic list. What follows is an example of that list. The elements of this list represent those subject areas that need attention at some point in the Lync project. Each of these elements has between three and 10 more sub-elements. In some cases, the sub-elements have tertiary elements. If a task needs to be at the quaternary level, I consider it for a move or maybe that I need to move its’ parent up a level. This avoids the issue of having too many project levels and getting lost in the weeds during planning; or worse yet, overlooking a project task. Remember that not all of these will apply to each project you do. And this list can be easily modified to meet core Exchange projects also.
1. Conduct Requirements discover
2. Design Lync 2010 Server System
3. Specify Client Deployment
4. Build Host Servers
5. Train the Trainer
6. Install SQL 2008 as two-node cluster
7. Install and configure 2 Lync EE FE servers as pool
8. Migrate existing R2 pool and users and component functionality
9. Remove existing R2 system
10. Install and configure HLB devices
11. Install and configure Monitoring and Archiving Lync Server roles using VM
12. Create Hyper-V specifications
13. Modify DNS
14. Modify External DNS
15. Assist with Certificates (External)
16. Assist with Internal PKI
17. Firewall rules
18. Configure ISA/TMG RP
19. Install and Configure Lync Edge Server pool
20. Define IP (internal and external)
21. Install and configure media gateway
22. Assist with Avaya PBX changes
23. Install, configure, & test Exchange UM
24. Create Dial Plan
25. Implement Dial Plan
26. Project Management
2010/12/01
Lync Server 2010 Documentation
Just in case you cannot find these docs elsewhere (and also so I don’t forget myself) – here are a few links to Lync Server documentation:
Microsoft Lync Server 2010 Archiving Deployment Guide
Microsoft Lync Server 2010 Monitoring Deployment Guide
Microsoft Lync Server 2010 Documentation Help File
Migrating from Office Communications Server 2007 R2 to Lync Server 2010
Microsoft Lync Server 2010 Enterprise Edition Deployment Guide
Enabling Quality of Service with Microsoft Lync Server 2010
Microsoft Lync Server 2010 Enterprise Voice Deployment Guide
Microsoft Lync Server 2010 Response Group Deployment Guide
Microsoft Lync Server 2010 Standard Edition Deployment Guide
Microsoft Lync Server 2010 Device Management and Troubleshooting Guide
Microsoft Lync Server 2010 Edge Server Deployment Guide
Microsoft Lync Server 2010 Client and Device Deployment Guide
Microsoft Lync Server 2010 Active Directory Guide
Microsoft Lync Server 2010 Call Park Deployment Guide
Microsoft Lync Server 2010 Reference: Call Data Recording and Quality of Experience Database Schema
Microsoft Lync Server 2010 Supportability Guide
Microsoft Lync Server 2010 Announcement Deployment Guide
2010/11/29
Zen Excellence
The master in the art of living makes little distinction between his work and play, his labor and his leisure, his mind and his body, his education and his religion.
He hardly knows which is which; he simply pursues his vision of excellence in whatever he does – leaving others to decide whether he is working or playing.
To him, he is always doing both.
2010/11/22
I am psyched!
I found out Friday that last July I was awarded MVP for Communications Server. Woo hoo!
I am totally wrapped around the axle on this!
2010/11/12
quotes
"Success consists of going from failure to failure without loss of enthusiasm."
Winston Churchill
2010/11/05
No ringback in Lync
I just did a deployment where the PSTN was a Nortel and we used an AudioCodes 1000 gateway. Everything worked out well until we noticed that outside calls coming through the Nortel got dead air until the Lync user either answered the call or Lync sent the call to voice mail.
Seeing as how Lync to Lync calls behaved properly, and tracing showed the proper SIP 180 responses, the obvious culprit was either the gateway or the Nortel. Turns out that in an AudioCodes gateway there is a setting for allowing ringback to leave the system and head for the PSTN!
Now, I am not a gateway guru, but don’t you think that would be a desired thing to have? Well, it is off by default. Flip it over a bit and voila! Ringback to PSTN.
2010/11/02
Lync Server 2010 IIS 7 prerequisites
IIS 7 webserver components for Lync FE
There are actually two ways do get this all done in one swoop. Using the GUI is good, but wouldn't you rather just do some cut n paste?
Note that there subtle differences here in the syntax although the individual feature add statements are the same.
For Server 2008 SP1 or SP2:
Open a command line (runas administrator). Then do the following (command will have wrapped):
servermanagercmd.exe -i web-common-http web-static-content web-http-errors web-http-redirect web-asp.net web-net-ext web-isapi-ext web-isapi-filter web-http-logging web-log-libraries web-http-tracing web-basic-auth web-windows-auth web-client-auth web-url-auth web-filtering web web-stat-compression web-mgmt-tools web-mgmt-console web-scripting-tools web-mgmt-compat web-metabase web-wmi web-lgcy-scripting web-lgcy-mgmt-console
For Server 2008 R2:
Open powershell (runas administrator), then do the following (again commands have wrapped here):
import-module servermanager
add-windowsfeature web-common-http, web-static-content, web-http-errors, web-http-redirect, web-asp-net, web-net-ext, web-isapi-ext, web-isapi-filter, web-http-logging, web-log-libraries, web-http-tracing, web-basic-auth, web-windows-auth, web-client-auth, web-url-auth, web-filtering, web-stat-compression, web-mgmt-tools, web-mgmt-console, web-scripting-tools, web-mgmt-compat, web-metabase, web-wmi, web-lgcy-scripting, web-lgcy-mgmt-console
2010/11/01
Lync Server 2010 SE Install
Now that we have the prerequisites installed, the CMS in place, the schema extended, and the topology built, here in part three we will continue through the SE install and take a first look at the Lync Control Panel.
To get started, return to the deployment wizard and select the “Install or Update Lync Server System.”
Notice that the first selection is to install the local configuration store. This is an important difference from OCS and the reason we needed to have the CMS installed and why we did the topology builder work. After that, the install proceeds very much like OCS, so I will not go into details. One note of importance: If you configured an element in topology builder, changes to the environment that involve that element will get changed in topology builder and re-published.
Note that at the end, the wizard shows you the powershell commands. Those who are seriously interested could reverse engineer these strings and do some serious learning. Moving on.
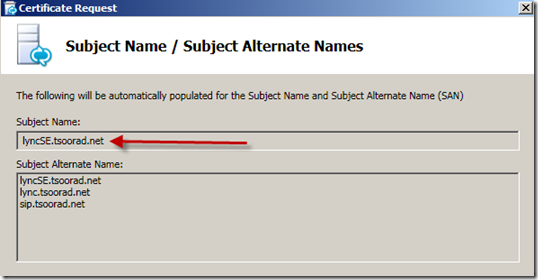
Now we are going to do the PKI for the SE. Remember the questions that were asked in the topology builder? Did you document your answers? Thankfully, if the answer is “no” you can simply open your topology builder and look. I am going to use a single name cert, and when the Reverse Proxy comes into being, I will redirect from public DNS name to internal fqdn. The Lync cert wizard is different from the OCS cert wizard, but nothing too weird.
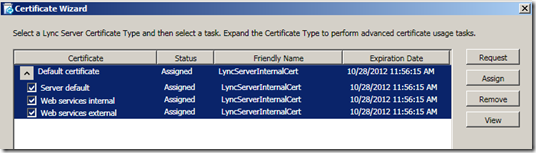
Notice how the wizard wants a cert for each function. After clicking no NEXT no less than five times I get to actually define my cert. I use the KISS method.
After that some basic cert info like who what where etc. Then we get this gem straight from the topology builder! Nice! However, if you are not planning on doing the RP redirect thing, you better know which name there corresponds to which. Remember that we left those boxes checked? Lync is going to look at the topology build in the CMS, as replicated to the local configuration store, and assign the certificate as needed. We have one cert, so there will be no issues. But if you use three different certs you may need to track things a bit closer.
On this next screen, read and understand. For my purposes all my answers are no, AND I already have sip.tsoorad.net defined on my topology so that name was already included. For those who use those expensive public certs, adding yet another domain name might just bump you to a more expensive cert. For those who are doing internal certs, but have multiple sip domains that meet the listed items, you better be prepared to hit the necessary check boxes.
A few more default “next” clicks and the certreq gets pushed to my internal EntCA.
We have a cert. Leave the “assign this certificate…” box checked and the wizard will assign the certificate as needed. In our case, the FE, and both web sites (internal and external).
After a few more obligatory “next” clicks we are finished with the cert request and assignment.
Almost done! Start the services.
Now, let’s take a quick tour of the Lync Control Panel. This is a Silverlight app. It is really pretty nice. We won’t go into great levels of detail here. Remember that we added a user to the CSAdministrator group in a previous section? You will need that user or another user of that group to operate the LCP and expect to be able to change things.
How pretty. One stop shopping. Sorta. Remember that many of the functions that were previously included in the R2 MMC are now configured in the Topology Builder and you will not find those items here. Take a review of the categories on the left hand side.
Users – self explanatory
Topology – no IP, certificates or anything like that. But you can start/stop, view replication, view settings, etc. This is where you go to drain a server.
IM and Presence – URL and File filter.
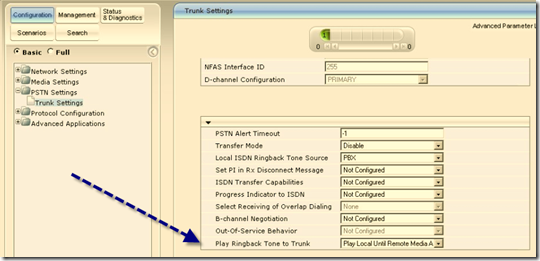
Voice Routing – Dial Plan, Voice Policy, Routes, PSTN Usage, Trunks, and a rudimentary Voice Route helper. You can export and import configurations from here. But only for voice elements, not the entire system.
Voice Features – Call Park and Unassigned numbers
Response Groups – Workflows, Queues, Groups
Conferencing – Policy, Meeting Configuration, Dial in Access, PIN Policy
Clients – Policy, Policy, Policy. In Lync, there is no ADM or GPO. All things are done either by the client manually or by the admin with policies.
External User Access – pay attention here. Policy, Access Edge Configuration (yes, as in affect how the Edge Server(s) act, Federation control, PIC.
Monitoring and Archiving – CDR, QoE, Archiving Policy, Archiving Configuration
Security – remember the Kerberos, NTLM security settings? and how to auth to the web components? and the Conferencing PIN policy (again)
Network Configuration – don’t get excited, this is not the system configuration, but all things Call Admission Control.
We have now installed the basic SE front end and looked at the control panel. In our next installment we will install the edge.
2010/10/26
Lync Server 2010 SE Install Part Two
So here we are with the basic prerequisites installed and the Topology Builder done.
Before too much more time goes by, we need to get AD DS tools in place so we can do the schema work. You can use the server manager GUI; I prefer a command line:
servermanagercmd.exe –i rsat-adds
This will complain a bit about being deprecated in 2008 R2, but it will work just fine. After a reboot, we’ll extend the schema, build our topology, publish the topology and be ready for Part Three where we will (finally) install the Lync Server 2010 Standard Edition.
Once you have that done, choose the Prepare First Standard Edition Server. This will setup the Central Management Service. You need this, and you cannot skip this step.
At this time, let’s extend the schema.
With the open install wizard:
This selection will produce the following menu of choices. Work your way down from the top. If you read instructions, you will notice that Microsoft cleverly numbered the steps.
My screen scrolls, and there is a step 6 and step 7 hiding. Whatever you do, do not ignore step 7. Trust me.
Alright! Here we are ready to deploy…
…but first you need to build up your topology. Let’s take a quick look at the bare bones of SE with Edge. Because this is in a lab, the IP scheme is a little funny what with all three IP subnets being private scopes, the TMG Reverse Proxy appears to be hanging off my larger domain (it is), and all my PKI will be done with my lab Enterprise CA. I don’t intend to show how or why specific topology items are the way they are, just that those items need definition to achieve our goal of an SE, with and Edge and being ready for EV.
The organization – take a look at the simplified URL’s…yes yes yes!
The site – this is a new concept. Notice that the federation route is here.
The SE pool screen 1 – the normal stuff:
The SE pool screen2:
Observe the separation of server roles here. This is important to keep your perspective. While we are doing an SE, with all roles combined, this is clearly setup for separate servers doing separate things in a highly available, heavy-duty environment. Look at the very bottom where you can see the inclusion of the “branch site” – another key change to Lync Server 2010.
Finally, look at the edge configuration. This is where the inbound next hop goes, as well as the IP addressing, enabling federation, and the NAT selection. Keep in mind that all roles get NAT]’d in Lync Server 2010. To make changes after your system is deployed, you will be visiting the topology builder again.
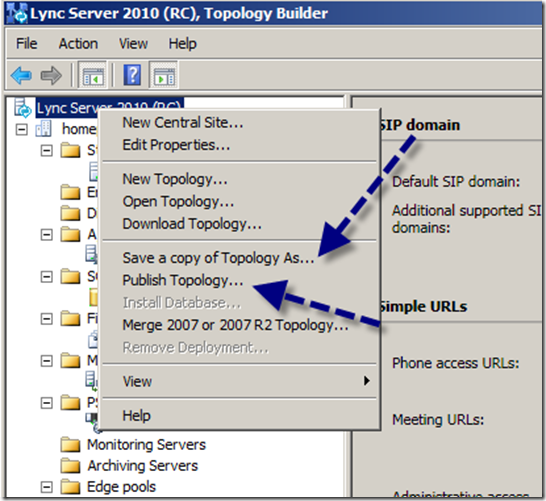
OK, enough messing around. Let’s publish this bad boy and move forward with installing bits that make this come to life. Right click the organization, and from the resulting menu, first save a file copy for future reference and then choose publish.
Read through all the various requirements (remember the CMS we installed in part one?) and then click Next.
In our case, there is only one CMS, so this choice is obvious. In a real-world scenario, there might well be multiple SE or EE pools and choices of hosts for the CMS that might not be on your SE host. Click next to move on.
Here we are in the midst of the blessed event. The entire publishing process can take a bit for the first time. Subsequent publishing events go fairly quickly.
Notice how the last little piece includes enabling the topology.
We now have extended the schema, installed the CMS, worked up a topology and published the topology, so now we are ready to install the bits and make all this work. In part three we will do that and also take a look at the new control panel.
edited note: I changed the title removing the “RC” part as the code went RTM just yesterday. This series will continue ahead with RC code. I do not anticipate significant changes with the install or planning processes.
2010/10/08
Lync Server 2010 Dialin Conferencing DMTF Controls
Finally.
In Conference DTMF Controls
DTMF
Feature
*6 Mute or unmute your microphone *****YES*****
*4 Toggle audience mute
*7 Lock or unlock the conference
*9 Enable or disable announcements for participants entering and exiting the conference
*3 Privately play the name of each participant in the conference
*1 Play a description of the available DTMF commands
*8 Admit all participants currently in the lobby to the conference
The DTMF commands listed above may differ based on the configuration on the Organizer's site. To ensure accuracy, please click on the "Find a local number" link in the invite for your meeting.
2010/10/07
RU1 to E2010 SP1
Out quickly with rollup 1 to sp1 for e2010. Notice “they” did not (at least in print) fix the various sp1 upgrade/install issues that were widely encountered…
2010/09/24
Lync Server 2010 RC SE Install
edited 29 Oct 2010 for IIS prereq changes
This is Part One of installing a Lync Server 2010 Standard Edition Environment.
We’ll get the prerequisites into place for a 2008 R2 server, and do the install up to the Topology Builder.
In the next part, we’ll take a look at the Topology Builder and install the Central Management Service.
After that we’ll get an Edge going too. Maybe later, if I can swing some hardware, we’ll demo some voice.
-------------------------------------------------------------------------
Lync Server 2010 Standard Edition does not have a lot of existing documentation available in the help file, and I know many peeps want to have a guide for installing this most basic component of Lync Server 2010. Let’s jump right in!
I am using x64 Server 2008 R2 running in VMWare.
This means that my install is done, and I have run all existing updates from Microsoft Update onto my server and then rebooted it. I have joined my domain. I am using a gawd account (domain admin, enterprise admin, schema admin) so I don’t have any permissions to worry about. I have also cranked the UAC down to nothing. Hey, this is a lab box, and it is behind a TMG, and you ain’t getting to it. No worries here. YMMV.
Because of the R2, we have the following prerequisites that must be met to install Lync Server 2010:
IIS7 with the following components:
For Standard Edition servers and Front End Servers, and Directors, the Microsoft Lync Server 2010 installer creates virtual directories in IIS for the following purposes:
- To enable users to download files from the Address Book Service
- To enable clients to obtain updates (for example, Microsoft Lync 2010)
- To enable conferencing
- To enable users to download meeting content
- To enable unified communications (UC) devices to connect to Device Update Service and obtain updates
- To enable users to expand distribution groups
- To enable phone conferencing
- To enable response group features
Lync Server 2010 requires the following IIS modules to be installed:
- Static Content
- Default Document
- HTTP Errors
- ASP.NET
- .NET Extensibility
- Internet Server API (ISAPI) Extensions
- ISAPI Filters
- HTTP Logging
- Logging Tools
- Tracing
- Windows Authentication
- Request Filtering
- Static Content Compression
- IIS Management Console
- IIS Management Scripts and Tools
- Tracing
- AnonymousAuthenticationModule
- ClientCertificateMappingAuthenticationModule
There are actually two ways do get this all done in one swoop. Using the GUI is good, but wouldn't you rather just do some cut n paste?
For Server 2008 SP1 or SP2:
Open a command line (runas administrator). Then do the following (command will have wrapped):
servermanagercmd.exe -i web-common-http web-static-content web-http-errors web-http-redirect web-asp.net web-net-ext web-isapi-ext web-isapi-filter web-http-logging web-log-libraries web-http-tracing web-basic-auth web-windows-auth web-client-auth web-url-auth web-filtering web web-stat-compression web-mgmt-tools web-mgmt-console web-scripting-tools web-mgmt-compat web-metabase web-wmi web-lgcy-scripting web-lgcy-mgmt-console
For those Server 2008 R2 folks: open powershell (runas administrator), then do the following - again command have wrapped here:
import-module servermanager
add-windowsfeature web-common-http, web-static-content, web-http-errors, web-http-redirect, web-asp-net, web-net-ext, web-isapi-ext, web-isapi-filter, web-http-logging, web-log-libraries, web-http-tracing, web-basic-auth, web-windows-auth, web-client-auth, web-url-auth, web-filtering, web-stat-compression, web-mgmt-tools, web-mgmt-console, web-scripting-tools, web-mgmt-compat, web-metabase, web-wmi, web-lgcy-scripting, web-lgcy-mgmt-console
Note that there subtle differences here in the syntax although the individual feature add statements are the same.
In addition (no you are not done yet!)
- IIS URL Rewrite module at http://go.microsoft.com/fwlink/linkid=197391
Important: If you are running Windows Server 2008 R2, you must install version 1.1 of the URL Rewrite module, available at http://go.microsoft.com/fwlink/?linkid=197394.
- IIS Application Request Routing module at http://go.microsoft.com/fwlink/?linkid=197392
You will also need:
.NET Framework 3.5.1 (right from the Server 2008 R2 install)
MSMQ (you will want this so you can do monitoring and archiving)(again, right from the Server 2008 R2 install)
Telnet client (used for troubleshooting)
Go get:
If you are doing just Server 2008 SP2, you will need MS KB 968929, "Windows Management Framework (Windows PowerShell 2.0, WinRM 2.0, and BITS 4.0)," at http://go.microsoft.com/fwlink/?linkid=197390 - this is not needed for 2008 R2.
And, because we want to play with everything, we need Windows Media Format Runtime also… for R2, we have the following zippy command line: (and yes it wrapped)
%systemroot%\system32\dism.exe /online /add-package /packagepath:%windir%\servicing\Packages\Microsoft-Windows-Media-Format-Package~31bf3856ad364e35~amd64~~6.1.7600.16385.mum /ignorecheck
For you 2008 SP2 fans, use this command: (wrapped)
%systemroot%\system32\pkgmgr.exe /quiet /ip /m:%windir%\servicing\Packages\Microsoft-Windows-Media-Format-Package~31bf3856ad364e35~amd64~~6.0.6001.18000.mum
My server wanted a reboot in the middle of all this because I ran the .NET updates into this also. You will want those, because there are several that fix some applications issues with Lync Server.
OK, so, we are pretty close! After doing all that, we execute the setup.exe found in the ISO under setup\amd64.
Say yes to the warning about The Microsoft Visual C++ 2008 redistributable being required to run Microsoft Lync Server 2010 communications software. If you install Lync Server 2010 by using the Lync Server Deployment Wizard, Setup prompts you to install this prerequisite, and it automatically installs it if it is not already installed on the computer. If you choose not to install it, Setup terminates. We don’t want that do we?
Now we are to this point:
Because I am in a lab VM, I take this and move on.
Accept the terms of the license agreement. If you don’t, you can’t install. Which brilliant lawyer figured that out?
After a couple of screen blinks, we get this:
Now, in R2, we’d blast ahead and prepare AD, but in Lync, we MUST have the topology builder. The topology builder is a great tool, does wonders for your success rate in deploying working solutions, and is needed later in your environment to make changes. Besides, Lync Server 2010 is not going to install if you don’t put the Topology Builder in place, and then export your complete plans first, so let’s just do it, OK?
Now, that wasn’t too bad?
This is what we get for our efforts…isn’t that pretty?
In our next installment, we’ll fire up the Topology Builder and get hot on installing our environment.
2010/09/17
Exchange 2010 SP1 curiosity(ies)
“(ies)” because there are mulitples.
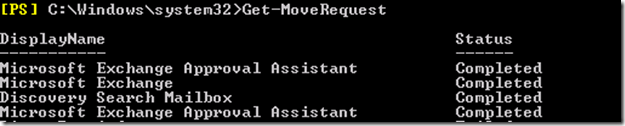
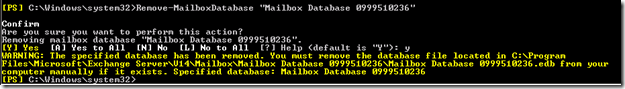
I went to remove the default mailbox database from a new e2010 sp1 install today. In the midst of the fun, I noticed that I still could not remove the database from the EMC. I had previously moved the arbitration mailboxes and the discover assistant mailbox.
But still, I got this error:
But, turning to the EMS proved very fruitful.
Wazzup wid dat? How can the GUI not allow the removal, but powershell yank it right out. The GUI is just a shell of the CLI. So what gives?
Also, note that GUI talks about set-mailboxplan and get-mailboxplan. Neither of those commands exist on the copy of Exchange 2010 SP1 that is running on this server. Nice, eh?
2010/09/15
Exchange 2010 public folder custom forms
Kudos to Dustin Rush, NAC Architecture
We are in the midst of an e2003-e2010 migration, and the customer has a custom contact form in the organization forms library. Regular public folder replication created the requisite public folder structure on the e2010. The custom form sort of worked in that new items in the contact list used the custom form, that data was intact, but viewing existing contact cards in the public folder reverted to the OOBE view.
Various efforts at enforcing the custom form from Outlook proved fruitless.
Dashing Dustin found this tool (DocMessageClass) that allowed us to modify the object attribute for each of the contacts in the public folder. The process took very little time – maybe 3-4 minutes for 10k+ objects.
2010/09/14
quotes
Michael Jordan:
"I've failed over and over and over again in my life and that is why I succeed."
Lou Holtz:
"Life is ten percent what happens to you and ninety percent how you respond to it."
2010/09/12
Spam spam spam spam
The Nigerian spam scam is making its’ rounds again. I’ve been seeing this in filters for the last month or so. Here is the first paragraph of what I received today:
Compliments of the day Sir,
How are you doing? Please this email is in regards to a consignment abandon which has been confiscated in your likely details etc, as the real approved receiving beneficiary from African delivering Company. we are running a scan text on this item to know why dropped before we discovered that it is a high valued and personal allocation, cash money is the content for delivering in your personal and company's favour hence this email. I have a scan copy result of Dubai airport detecting machine and can prove it.
Just for an eyeball test, how many grammar errors can you find in this short cut? But, the scary part is not the bad grammar. The scary part is that this spam is showing up because somebody is saying “wow, my lucky day!” and actually responding to this and following through, and losing their money. This spam exists because if the numbers are big enough, even the 1/2 of one percent (or whatever the return is) is worth it to the originator.
Can people really be THAT stoopid?
2010/09/01
Default Exchange 2010 RBAC groups
I had to look this up the other day – and I did not think it was all that easy to figure, so I made up this little table so I could get my head around the DEFAULT RBAC groups. Keep in mind that the base recommendation is to create your own groups to match your specific requirements. This table illustrates the what comes OOBE and represents some great starting points for understanding what is going on under the hood with RBAC.
| Built-in RBAC Group | Functionality | Default assigned roles | Default Members | ||||||||||
| Delegated Setup | Members of this management role group have permissions to install and uninstall Exchange on provisioned servers. This role group shouldn't be deleted. | View-Only Configuration | None | ||||||||||
| Discovery Management | Members of this management role group can perform searches of mailboxes in the Exchange organization for data that meets specific criteria. |
| None | ||||||||||
| Help Desk | Members of this management role group can view and manage the configuration for individual recipients and view recipients in an Exchange organization. Members of this role group can only manage the configuration each user can manage on his or her own mailbox. Additional permissions can be added by assigning additional management roles to this role group. |
| None | ||||||||||
| Hygiene Management | Members of this management role group can manage Exchange anti-spam features and grant permissions for antivirus products to integrate with Exchange. |
| FQDN of server | ||||||||||
| Public Folder Management | Members of this management role group can manage public folders. Members can create and delete public folders and manage public folder settings such as replicas, quotas, age limits, and permissions as well as mail-enable and mail-disable public folders. |
| Exchange Public Folder Administrators | ||||||||||
| Recipient Management | Members of this management role group have rights to create, manage, and remove Exchange recipient objects in the Exchange organization. |
| Exchange Recipient Administrators | ||||||||||
| Records Management | Members of this management role group can configure compliance features such as retention policy tags, message classifications, transport rules, and more. |
| None | ||||||||||
| Server Management | Members of this management role group have permissions to manage all Exchange servers within the Exchange organization, but members don't have permissions to perform operations that have global impact in the Exchange organization. |
| None | ||||||||||
| UM Management | Members of this management role group can manage Unified Messaging organization, server, and recipient configuration. |
| None | ||||||||||
| View-Only Organization Management | Members of this management role group can view recipient and configuration objects and their properties in the Exchange organization. |
| Exchange View-Only Administrators | ||||||||||
| Organization Management | Members of this management role group have permissions to manage Exchange objects and their properties in the Exchange organization. Members can also delegate role groups and management roles in the organization. This role group shouldn't be deleted. | Active Directory Permissions, Address List, Audit Logs, Cmdlet Extension Agents, Database Availability Groups, Database Copies, Databases, Disaster Recovery, Distribution Groups, Edge Subscriptions, E-Mail Address Policies, Exchange Connectors, Exchange Server Certificates, Exchange Servers, Exchange Virtual Directories, Federated Sharing, Information Rights Management, Journaling, Legal Hold, Mail Enabled Public Folders, Mail Recipient Creation, Mail Recipients, Mail Tips, Message Tracking, Migration, Monitoring, Move Mailboxes, Organization Client Access, Organization Configuration, Organization Transport Settings, POP3 And IMAP4 Protocols, Public Folder Replication, Public Folders, Receive Connectors, Recipient Policies, Remote and Accepted Domains, Retention Management, Role Management, Security Group Creation and Membership, Send Connectors, Transport Agents, Transport Hygiene, Transport Queues, Transport Rules, UM Mailboxes, UM Prompts, Unified Messaging, User Options, View-Only Configuration, View-Only Recipients | Exchange Organization Administrators |
2010/08/19
LM and OC password lockout
A bit of trivia I discovered today. The OC client and the LM client are sort of linked at the hip. I backed into this via Outlook and the LM addin…because I got locked out of my office account while testing the client’s install. Something got bollixed up with the passwords…and here is what happened.
While doing some testing I had to change the login account on my OC. I noticed that when I did that, the LM client picked up the change. Nice!
But alas! the password in the LM client account setup remains as the previous login…
Naturally, this resulted in the account being locked out for password failure. So, while the LM did pick up the user name change, it bombed on the password.
Also, note that this is different depending on which way you work it…certainly not a two way street. In the first scenario, I changed the username from OC, and LM picked up the change but not the password. Going the other way is even worse; changing the username in LM only sent the sign-in name to OC client… the underlying verification stayed the same in both clients – and both were wrong. In addition, the LM had the password from the other account!
Let’s hope this get’s fixed in CS 2010 where the LM and OC are one client.
disable “Schedule a Conference Call” button in Outlook LM plugin
I got asked today on how to do this. Being as clueless as I am, I started with a little research. Doggoned if I didn’t hit paydirt after only a few reads. This is good stuff, so I want to make sure that I don’t lose it.
See this article here for the original material – figures there would be a KB for this. I am reposting here for my own edification.
There is a registry entry that can be used to disable this button:
1. Locate and then click to select the following registry subkey:
HKEY_LOCAL_MACHINE\Software\Microsoft\Live Meeting\Addins
Note Use this subkey for x86-based systems. If you are running a x64-based system, locate and click the following subkey:
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Live Meeting\Addins
2. After you select the subkey that is specified in step 3, point to New on the Edit menu, and then click DWORD Value.
3. Type RemoveConferenceCall, and then press ENTER.
4. Right-click RemoveConferenceCall, and then click Modify.
5. In the Value data box, type 1, and then click OK.
6. On the File menu, click Exit to close Registry Editor.
Change the Value to 0 and the button will be available again.
A full list of livemeeting registry keys can be found here: http://technet.microsoft.com/en-us/library/dd637135(office.13).aspx
2010/07/29
quote o’ da day
"Giving money and power to government is like giving whiskey and car keys to teenage boys."
P.J. O’Rourke
2010/07/24
Reveal hidden devices server 2008
I do a lot of lab work. I use virtual images. I build the base image and then copy/move as needed. Recently, I took an entire lab build and needed to start it on a new VM host.
The first 2008 DC I started told me that I could not rename the NIC because “…a connection with the name specified already exists.”
Found this article here, which fixed me right up. The relevant portions are included for reference.
| The following procedure will show no-longer-connected devices in Device Manager for Server 2008. Open a command window with elevated privileges (Start -> Right-click "Command Prompt", select "Run as Administrator") In the command window, execute the following commands: SET DEVMGR_SHOW_NONPRESENT_DEVICES=1 The second command starts the Device Manager. It MUST be started from the elevated-privilege command window for this procedure to work. In Device Manager, click the VIEW menu item and select "Show hidden devices". This should show any hidden devices. For network adapters, expand the network adapters node. Right-Click any device you wish to remove, and click Uninstall. |
2010/07/21
single cert for ocs/exchange
this is a rewrite of previous post that got thrown away somehow…
Single certificate for OCS/Exchange firewall usage
Certificates can be complicated to understand, difficult to manage, and if you don’t have an internal PKI structure, downright expensive as you move forward with more and more dynamic applications that extend your Unified Communications to your remote users and business partners.
Internal certificates work wonders for your Active Directory Domain Services members. For Unified Communications, where OCS and Exchange are going to be using the same ISA 2006 server as the firewall, utilizing a Subject Alternative Name (SAN) certificate for your edge configuration and your ISA configuration can save you time, management hassles, and possibly provide cost savings as well. For internal servers, an internal PKI is just fine, but for the public interface of your system, you should most likely be looking at using a public-sourced key such as Go-Daddy, Thawte, DigiCert, etc. OCS Federation, remote users, and Public Instant Messaging Connectivity (PIC) demand public certificates. I know that I do not want to ship my internal CA root certificate to a slew of administrators and expect them to get that certificate into the correct spot for our systems to co-exist. But I digress.
The following table shows the SAN names needed on a certificate to support the base OCS and Exchange functions on ISA 2006/TMG/UAG – and I imagine that this certificate construction will work just fine on many other firewalls as well. The table comes from my test domain; you should replace my test domain with your own domain name.
Obtain a public SAN (UCC) certificate from your favorite provider; import the certificate into your OCS Edge server and your ISA server computer account Trusted Root Certificate store and then you can use one certificate for all these uses. This approach leaves you with only the one certificate to manage and renew, or, if life treats you badly, move to a new server.
|
| SAN Name (what URL?) | Usage | Notes |
| 1 | SIP.tsoorad.net | OCS Edge Server | IM, Presence, Federation, PIC |
| 2 | LM.tsoorad.net | OCS Edge Server | Web Conferencing |
| 3 | AV.tsoorad.net | OCS Edge Server | A/V |
| 4 | OCS.tsoorad.net | ISA Reverse Proxy | Web Components |
| 5 | CWA.tsoorad.net | ISA Web Listener | Communicator Web Access |
| 6 | DOWNLOAD.CWA.tsoorad.net | ISA Web Listener | Cname for CWA desktop sharing |
| 7 | AS.CWA.tsoorad.net | ISA Web Listener | Cname for CWA desktop sharing |
| 8 | MAIL.tsoorad.net | ISA publisher | Outlook Anywhere, EAS, OWA, POP, IMAP |
| 9 | AUTODISCOVER.tsoorad.net | ISA Web Listener | Autodiscover is used by outlook and OCS. |
2010/07/14
Evolution II
For those that don't know about history...here is a
condensed version.
Humans originally existed as members of small bands of nomadic hunters/gatherers. They lived on deer in the mountains during the summer and would go to the coast and live on fish and lobster in the winter.
The two most important events in all of history were the invention of beer and the invention of the wheel. The wheel was invented to get man to the beer. These were the foundation of modern civilization and together were the catalyst for the
splitting of humanity into two distinct subgroups:
- Liberals
- Conservatives.
Once beer was discovered, it required grain and that was the beginning of agriculture. Neither the glass bottle nor aluminum can were invented yet, so while our early humans were sitting around waiting for them to be invented, they just stayed close to the brewery. That's how villages were formed.
Some men spent their days tracking and killing animals to BBQ at night while they were drinking beer. This was the beginning of what is known as the Conservative movement...
Other men who were weaker and less skilled at hunting learned
to live off the conservatives by showing up for the nightly BBQ's and doing the sewing, fetching, and hair dressing. This was the beginning of the Liberal movement.
Some of these liberal men eventually evolved into women. They
became known as girlie-men. Some noteworthy liberal achievements include the domestication of cats, the invention
of group therapy, group hugs, and the concept of Democratic
voting to decide how to divide the meat and beer that
conservatives provided.
Over the years conservatives came to be symbolized by the largest, most powerful land animal on earth, the elephant. Liberals are symbolized by the jackass for obvious reasons.
Modern liberals like imported beer (with lime added), but most prefer white wine or imported bottled water. They eat raw fish but like their beef well done. Sushi, tofu, and French food are standard liberal fare.. Another interesting evolutionary side note: most of their women have higher testosterone levels than their men. Most social workers, personal injury attorneys, journalists, dreamers in Hollywood and group therapists are liberals. Liberals invented the designated hitter rule because it wasn't fair to make the pitcher also bat.
Conservatives drink domestic beer, mostly Bud or Miller. They eat red meat and still provide for their women. Conservatives are big game hunters, rodeo cowboys, lumberjacks, construction workers, firemen, medical doctors, police officers, engineers, corporate executives, athletes, members of the military, airline pilots and generally anyone who works productively. Conservatives who own companies hire other conservatives who want to work for a living.
Liberals produce little or nothing. They like to govern the producers and decide what to do with the production. Liberals believe Europeans are more enlightened than Americans. That is why most of the liberals remained in Europe when conservatives were coming to America . They crept in after the Wild West was tamed and created a business of trying to get more for nothing.
Here ends today's lesson in world history.
2010/07/12
stupidity reigns
The scary part about this is not that I received the item of UCE (SPAM)(junk mail)(whatever), but that this shit exists because there are people stupid (as opposed to ignorant – look up the difference for yourself) to the point that they will get this in their email and say “wow! I had better respond right now!” and send their PIP off into the ether. Really?! Just on the sentence construction alone this is a scam. However, this activity only occurs because someone is turning a profit doing so.
And both side of this are allowed to breed. I vote for culling the gene pool.
Spam sample follows:
| ANTI-TERRORIST AND MONETARY CRIMES DIVISION FBI HEADQUARTERS IN WASHINGTON, D.C. FEDERAL BUREAU OF INVESTIGATION J. EDGAR HOOVER BUILDING 935 PENNSYLVANIA AVENUE, NW WASHINGTON, D.C. 20535-0001 DATE 9 7 20 10 ATTENTION: F. B .i This is not a child play, we are ready to take you to any length if you failed to proof the legitimate of the fund you are about to receive. As a Federal Commission we are here to protect your interest and the interest of all the United State citizens as well as this great Nation. You have been investigated as the beneficiary of the said funds that is why you are in touch with the FBI for a solid proof before the funds will be release to you. The said funds is now in U.S Bank in your name which has been placed on hold under the custody of the FBI for further verification and proof before releasing the fund to you. You do not have this document in your files, if you did the fund would not have been hold. We did not believe this at first, but when we saw the transfer we had no option than to contact you. We have gone through your Identification record and also the information received from you, we have verified a lot of things about you. It has come to the attention of our Money Trafficking investigation department, that you have some funds valued at U.S $10,000.000.00 to your name, The said payment is awaiting adjudication and crediting to you this funds are from Inheritance "willed " from C.B.N Bank Nigeria precisely. With full concern of The F.B.I and the Internal Revenue Service (IRS) wish to remind you of the consequences of remitting such huge sums of money without complying fully with the provisions of the Financial and Allied Matters Decree 5 as amended in sub-section C (6) of 2003, which stipulates that any monitory transaction been done in the United States Of America, must have proper records, which duly guarantees and covers the transaction as legitimate and legally acquired and not criminally or terrorist associated funds. This is due to ongoing terrorist activities/economic crimes on and against the United States of America citizens. Note that with the information’s we have here, the fund in your name here was release from Federal Republic Of Nigeria. To this regard you are to contact the FBI Nigeria where the fund was release from so that they will issue you the required document because they are the only people that can issue you the document. Nobody else have the right or privilege to issue you this document unless the FBI Nigeria. You are under an observational /Investigation in connection with money laundering. If your funds comes from a legitimate and legal source, the proper guidelines for you to recover the right of transaction is for you to provide the official monitory transaction release document so that your funds will be legally processed and recorded and accounted for and then finally released to you. FEDERAL BUREAU OF INVESTIGATION (ANTI-TERRORIST AND MONEY LAUNDERING DEPARTMENT) IS HERE to wipe out terrorism, and will stop at no length in doing our duty for the American people. You have 48 hours to produce legal proof of the below frozen wired transaction number coded: 34567112 .... 39AZQV9007 owned by you. You do not have any rights to receive these funds if the documented legal wire information is not complete. For your own good and benefit, you are advice not to send your money to anybody. It have come to our notice that you have been dealing with scammers regarding the present transaction in your name, with the power imposed on us as a high Federal Commission, you are hereby warn and instruction to terminate your involvement with any people or individual contacting you regarding this present transaction.The said funds is now in our custody in your name as the beneficiary, your dealings should be channel to this office alone, if we find out you are still communicating with Imposters you will be charge for advance fraud communication by the Federal Law. The very heart of FBI operations lies in our investigations--which serve, as our mission states, "to protect and defend the United States against terrorist and foreign intelligence threats and to enforce the criminal laws of the United States." So follow our instructions properly to avoid any action before you. We currently have jurisdiction over violations of more than 200 categories of federal law. So you can see that we can track you down through Investigative programs. We have your address and the evidence and status of your wired funds, so we can arrest you anytime anywhere. Be inform that the funds under the custody of the FBI was confirmed in your name as the beneficiary, according to the Federal Commission, it is mandatory by law you proof the legitimate of the funds in your name by providing the required document to us, failure to comply with the FBI law, legal action will follow according to the FBI United State Federal Constitution. You dont have the required document in your possession, this document are only to be issue to you from the paying country NIGERIA, to this regards you are advice to contact the FBI NIGERIA to obtain the document from them to enable the immediate release of the funds in your name. We have done our verification on your FBI Identification Record with our Social Security Number, the only document left is the required Diplomatic Immunity Seal Of Transfer (DIST) Which should be issue to you from the paying country of the said funds, you are to contact the Federal Bureau Of Investigation(FBI) Nigeria to obtain the above required document, find below their contact information's: Contact Person: Mrs Vivian Royd Email: vivian_royd@yahoo.com <mailto:vivian_royd@yahoo.com> Furthermore, be advice that according to the United State Law together with the FBI rules and regulations, you are to obtain the document from the FBI Nigeria where the fund was transfer from. Also Note that you are to take care of the Document to be issued to you right away, because due to the content of the document and how important and secured the document is, You are to take care of the document by sending to the FBI Nigeria the sum of $250.00 Dollars only for the issuing of the document right away. That is the only way the FBI Nigeria will issue you the document, because they are going to issue you the Authentic and Original copy of the document. You are here by advice to Contact them through the email address above to acquire from them on how you are going to send the fee to them. Note that you are to do this immediately if you really want your fund to be credited to your personal account and also if you don’t want any action to be fall before you. We have already informed the FBI Nigeria about the present situation, so go ahead and contact them immediately. Your fund is now on our custody and will not be release to you unless the required document is confirmed, After that the fund will be release to you immediately without any delay. NOTE: We have asked for the above documents to make available the most complete and up-to date records possible for no criminal justice purposes. WARNING: failure to produce the above requirement, legal action will be taken immediately by arresting and detaining you, justificated and if found guilty, you will be jailed. As terrorism, drug trafficking and money laundering is a serious problem in our community today. The F.B.I will not stop at any length in tracking down and prosecuting any criminal who indulge in this criminal act. FORWARD THE DOCUMENT TO US VIA EMAIL ATTACHMENT AS SOON AS YOU OBTAIN IT. Faithfully Your's FBI Director Robert S. Mueller, III |
frontier sucks part five
Well, ticket was opened on 1 July. Here we are 12 days later. No one has called me. I was told 11 days ago that someone would call me and resolve this issue “tomorrow.” That did not happen.
quotes of da day
“I might be beat on talent, but not on effort”
“Good things happen when you up your effort level”
2010/06/28
Move e2k3 database manually
Today a client asked me to outline the methods for moving his Exchange 2003 EDB/STM database off of his drive that was going bad. The ESM directed move was stuck at 100% but was not completeing. The database/STM in question was about 80GB. What happens is that the GUI says done, but the eseutil in the background is still running, and will be for many hours.
There is a manual method – unsupported, but it works nicely.
It has been a long while since I did this, so I decided to get it documented and published so others can find this data also. Keep in mind that this method is NOT supported by the vendor, and YMMV. However, I have used this many times very successfully. The reason behind this are the slowness at which database moves occur from within the ESM. Slow does not describe it!
· Exchange 2003 will move about 4GB per hour on fast drives.
· This method allows you to use file copy which goes much quicker.
· For a 20GB databases, I have used this method to move the databases in less than 1 hour - an ESM move would have taken over 5 hours.
· 15k SCSI drives will go faster than network, iSCSI, or SATA.
KNOW what filenames you are working with. Exchange expects the filenames to be EXACT. When you do these moves, copies and renames, make SURE that you are using the names that Exchange is wanting to see. Check in the ESM BEFORE you start this process. I suggest screen shots, writing down notes, etc. Guessing at this information later will not be fun.
1. Dismount databases
2. Stop the stores
3. Copy the edb and stm to location 'x'
4. Crc check the original against location 'x' to ensure file copy successful (use http://www.febooti.com/products/filetweak/screenshots/calculate-hash-crc-checksum.html or similar)
5. Remove the original files from original location.
- Suggest a simple rename to keep the files in place.
6. Start Store
7. Mount database. It will come up and say there is no file, creating a blank will lose data, etc. Say yes to that.
8. You will have BLANK DATABASES at this point. ZERO mailboxes. DO NOT ATTEMPT TO LOGIN.
9. Using ESM standard tools. MOVE the databases to location "y"
a. This will complete very quickly as you have 5mb, empty databases.
10. Dismount databases
11. Stop store.
12. Move location 'x' files into location 'y'
- If you did the ESM database move to location ‘x’ then you can just rename the files.
13. Start store
14. Mount databases.
15. Finish. Login and test.
2010/06/23
iPhone VM & Exchange
A day late and a dollar short…
I have been using my iPhone for VM and I had forgotten how I set the mailbox for iPhone support. So I flailed around a bit and then remembered that Tom Pacyk had the info on his blog….
And now it will be here also, so idiots like me don’t forget where to find the info.
set-ummailbox identity –callansweringcodec gsm
You can use g711 also, but it makes huge files.
Exchange 2010 does MP3 as the default, I believe, audio files for VM so this should not be an issue if you have Exchange 2010.
2010/04/13
2010/03/31
OCS 2007 R2 and Server 2008 R2
Concerning supportability of OCS 2007 R2 and Server 2008 R2 hosts and Server 2008 R2 Active Directory domains…
MS KB 982020 and MS KB 982021 outline what it takes to have OCS 2007 R2 operate successfully with Server 2008 R2 AD and to be hosted by 2008 R2 servers.
2010/03/05
DCOM error 10009 and certificate requests
I spent the entire day learning and relearning things about ISA, TMG, and Windows Firewall. This took me way more time than I wanted which highlights the three basic troubleshooting starting points. I chose the wrong starting point, and then I chose the next starting point wrongly also. Of the three choices, of course it was the last choice (midpoint and work towards one end) that proved to be the winner. Turns out that TMG/ISA/WF all had a part in this. WF was the culprit on the CA, because there is a rule that needs enabling and by default it is not. TMG/ISA was also an issue, because of the way RPC traffic is filtered. Even if you have a wide-open rule that says “let everything go from spot A to spot B” RPC traffic gets hosed. Argh.
Suffice it to say, I have finally resolved my issue, and an ISA/TMG specialist will probably think I am a loser, but WTH, here goes.
The problem was that I could not request a cert from the OCS R2 MMC. The CA was across a VPN (TMG/ISA). First little bit was finding out that, for security, the Windows Firewall disables COM+ access by default. Now, you would think, that following the MSFT paradigm of enabling Windows Firewall rules when the feature/role/application is installed, that installing a CA on the server would turn this on, but noooOOOOOoooo!
You have to enable this rule - in my case this was a ws08r2 DC with the EntCA installed on it. You don’t need to do this on the requestor, but the target of the request. So, my OCS FE was requesting a cert from the CA on the DC. Therefore, on the CA, enable the Com+Network Access (DCOM-In) rule:
Then, because of the VPN link involved, on BOTH sides of the link, the rule that allows the traffic from the internal to the VPN target needs to have the RPC traffic filter disabled. There is a GREAT article here that I found that finally resolved my issue. This is the piece of that article that did it for me:
- If ISA Server is requesting the certificate, disable the "Enforce strict RPC compliance setting" on the system policy rule. To do this, on the Firewall Policy tab of ISA Server Management, click Edit System Policy on the Tasks tab. Select the Active Directory group in the Configuration Groups list. On the General tab, clear the Enforce strict RPC compliance checkbox.
- If an internal host is requesting the certificate from another network through ISA Server, do the following: in the Firewall Policy tab of ISA Server Management, right-click the access rule allowing the traffic, and then click Configure RPC protocol. On the Protocol tab, clear Enforce strict RPC compliance.
What that means visually on the TMG/ISA side :
I hope this helps you in some small way. Now, back to the job I was supposed to get done this morning!
-
Background About four months ago, I made the decision to extend my lab, Tsoorad.net, out to the larger world of the internet. I have sever...
-
Do you need to test outbound calling to international numbers but your customer doesn’t have anyone just sitting there waiting for your call...
-
Edited 10.29.2012 1535 PST – thanks to Jeremy! Scenario I recently did a project where the client wanted to use their email address domain...